
The 312-50V12 exam is hard to pass, but you don’t want to continue wasting time and money by retaking it to get the score you want, so what to do? The 312-50v12 dumps are a successful passbook for the (CEHv12) exam.
The 312-50v12 dumps can prepare and arm you with enough knowledge, skills, and confidence to take the exam to get you a high score on the CEHv12 exam. Especially the latest 312-50v12 dumps https://www.pass4itsure.com/312-50v12.html from the Pass4itSure website!
The latest 312-50V12 exam knowledge points
In order not to waste time, here I will only provide a link where you will see comprehensive information.
Certified Ethical Hacker Exam (EC-COUNCIL CEHv12): https://www.eccouncil.org/certified-ethical-hacker-training-and-certification/
312-50V12 exam preparation: provides advice on exam preparation
Use the 312-50V12 dumps provided by Pass4itSure to prepare for the exam, which is the most important general direction
First, master the syllabus:
You should download the syllabus, which is the scope of the exam, and prepare purposefully around the syllabus. The link has been provided above, pay attention to the view.
Secondly, take classes:
USE THE OFFICIAL TUTORIAL OF THE EC-COUNCIL DIRECTLY. It turns out that this is a faster way to master the test center.
Finally, do the questions:
Practice questions are necessary not only to promote knowledge of CEHv12 but also as part of the CEHv12 exam.
Experience sharing: Share strategies and tips for the 312-50V12 exam
If you need to take the Certified Ethical Hacker Exam (CEHv12), the latest CEHv12 dumps are essential, in addition to that, a good mindset and diligent practice are also important.
Pass4itSure 312-50V12 dumps will be available for you:
- High-quality relevant learning materials.
These materials are available in two forms PDF+VCE for easy learning.
As a reminder, make sure the learning materials you will be using are accurate and up-to-date. This ensures that the information you know is correct and up-to-date.
- You can take a mock test.
An important part of the mock test preparation project. You need a lot of practice.
Practice resources: next, share some of the latest free 312-50v12 dumps exam questions
Question 1:
Richard, an attacker, aimed to hack loT devices connected to a target network. In this process. Richard recorded the frequency required to share information between connected devices. After obtaining the frequency, he captured the original data when commands were initiated by the connected devices.
Once the original data were collected, he used free tools such as URH to segregate the command sequence. Subsequently, he started injecting the segregated command sequence on the same frequency into the loT network, which repeats the captured signals of the devices.
What Is the type of attack performed by Richard In the above scenario?
A. Side-channel attack
B. Replay attack
C. CrypTanalysis attack
D. Reconnaissance attack
Correct Answer: B
Replay Attacks could be a variety of security attacks on the info sent over a network. In this attack, the hacker or a person with unauthorized access captures the traffic and sends a communication to its original destination, acting because of the original sender.
The receiver feels that it\’s an Associate in Nursing genuine message however it\’s the message sent by the aggressor. the most feature of the Replay Attack is that the consumer would receive the message double, thence the name, Replay Attack.
Prevention from Replay Attack:
1. Timestamp technique prevention from such attackers is feasible if the timestamp is employed at the side of the info. Supposedly, if the timestamp on information is over a precise limit, it may be discarded, and the sender may be asked to send the info once more.
2. Session key technique nother way of hindrance, is by the victimization session key. This key may be used one time (by sender and receiver) per dealing, and can\’t be reused.
Question 2:
You have successfully logged on to a Linux system. You want to now cover your trade Your login attempt may be logged on several files located in /var/log. Which file does NOT belongs to the list:
A. user.log
B. auth.fesg
C. wtmp
D. btmp
Correct Answer: C
Question 3:
You are tasked to configure the DHCP server to lease the last 100 usable IP addresses in subnet to. 1.4.0/23. Which of the following IP addresses could be teased as a result of the new configuration?
A. 210.1.55.200
B. 10.1.4.254
C. 10..1.5.200
D. 10.1.4.156
Correct Answer: C
https://en.wikipedia.org/wiki/Subnetwork As we can see, we have an IP address of 10.1.4.0 with a subnet mask of /23. According to the question, we need to determine which IP address will be included in the range of the last 100 IP addresses.
The available addresses for hosts start with 10.1.4.1 and end with 10.1.5.254. Now you can see that the last 100 addresses include the address 10.1.5.200.
Question 4:
Kevin, an encryption specialist, implemented a technique that enhances the security of keys used for encryption and authentication. Using this technique, Kevin input an initial key to an algorithm that generated an enhanced key that is resistant to brute-force attacks.
What is the technique employed by Kevin to improve the security of encryption keys?
A. Key derivation function
B. Key reinstallation
C. A Public key infrastructure
D. Key stretching
Correct Answer: D
Question 5:
Bill has been hired as a penetration tester and cyber security auditor for a major credit card company. Which information security standard is most applicable to his role?
A. FISMA
B. HITECH
C. PCI-DSS
D. Sarbanes-OxleyAct
Correct Answer: C
Question 6:
which of the following information security controls creates an appealing isolated environment for hackers to prevent them from compromising critical targets while simultaneously gathering information about the hacker?
A. intrusion detection system
B. Honeypot
C. Botnet
D. Firewall
Correct Answer: B
Question 7:
You are a security officer of a company. You had an alert from IDS that indicates that one PC on your Intranet is connected to a blacklisted IP address (C2 Server) on the Internet. The IP address was blacklisted just before the alert.
You are starting an investigation to roughly analyze the severity of the situation. Which of the following is appropriate to analyze?
A. IDS logs
B. Event logs on a domain controller
C. Internet Firewall/Proxy log.
D. Event logs on the PC
Correct Answer: C
Question 8:
Vlady works in a fishing company where the majority of the employees have very little understanding of IT let alone IT Security. Several information security issues that Vlady often found include, employees, sharing passwords, writing his/her password on a post-it note and sticking it to his/her desk, leaving the computer unlocked, didn\’t logging out from emails or other social media accounts, etc.
After discussing with his boss, Vlady decided to make some changes to improve the security environment in his company. The first thing that Vlady wanted to do is to make the employees understand the importance of keeping confidential information, such as password, a secret and they should not share it with other persons.
Which of the following steps should be the first thing that Vlady should do to make the employees in his company understand to importance of keeping confidential information a secret?
A. Warning to those who write the password on a post-it note and put it on his/her desk
B. Developing a strict information security policy
C. Information security awareness training
D. Conducting a one-to-one discussion with the other employees about the importance of information security
Correct Answer: A
Question 9:
Firewalls are software or hardware systems that can control and monitor the traffic coming in and out of the target network based on a pre-defined set of rules. Which of the following types of firewalls can protect against SQL injection attacks?
A. Data-driven firewall
B. Packet firewall
C. Web application firewall
D. Stateful firewall
Correct Answer: C
https://en.wikipedia.org/wiki/Web_application_firewall A web application firewall (WAF) is a specific form of application firewall that filters, monitors, and blocks HTTP traffic to and from a web service. By inspecting HTTP traffic, it can prevent attacks exploiting a web application\’s known vulnerabilities, such as SQL injection, cross-site scripting (XSS), file inclusion, and improper system configuration.
Question 10:
One of your team members has asked you to analyze the following SOA record.
What is the TTL? Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600 3600 604800 2400.)
A. 200303028
B. 3600
C. 604800
D. 2400
E. 60
F. 4800
Correct Answer: D
Question 11:
You have gained physical access to a Windows 2008 R2 server which has an accessible disc drive. When you attempt to boot the server and log in, you are unable to guess the password. In your toolkit, you have an Ubuntu 9.10 Linux LiveCD. Which Linux-based tool can change any user\’s password or activate disabled Windows accounts?
A. John the Ripper
B. SET
C. CHNTPW
D. Cain and Abel
Correct Answer: C
Question 12:
Which protocol is used for setting up secure channels between two devices, typically in VPNs?
A. PEM
B. ppp
C. IPSEC
D. SET
Correct Answer: C
Question 13:
You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c
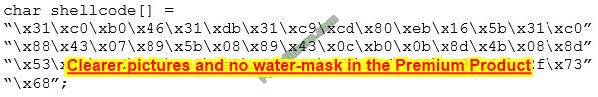
What is the hexadecimal value of NOP instruction?
A. 0x60
B. 0x80
C. 0x70
D. 0x90
Correct Answer: D
Question 14:
A newly joined employee. Janet has been allocated an existing system used by a previous employee. Before issuing the system to Janet, it was assessed by Martin, the administrator. Martin found that there were possibilities of compromise through user directories, registries, and other system parameters.
He also Identified vulnerabilities such as native configuration tables, incorrect registry or file permissions, and software configuration errors. What is the type of vulnerability assessment performed by Martin?
A. Credentialed assessment
B. Database assessment
C. Host-based assessment
D. Distributed assessment
Correct Answer: C
Question 15:
When you are getting information about a web server, it is very important to know the HTTP Methods (GET, POST, HEAD, PUT, DELETE, TRACE) that are available because there are two critical methods (PUT and DELETE).
PUT can upload a file to the server and DELETE can delete a file from the server. You can detect all these methods (GET, POST, HEAD, DELETE, PUT, TRACE) using the NMAP script engine. What Nmap script will help you with this task?
A. HTTP-methods
B. HTTP enum
C. HTTP-headers
D. HTTP-git
Correct Answer: A
If you want to fulfill your dream of achieving CEH v12 certification, be sure to make finding a reputable and authentic 312-50v12 dumps your top priority.
To give you a scheme. Download the latest Pass4itSure 312-50V12 dumps https://www.pass4itsure.com/312-50v12.html and use them wisely to help you pass the 312-50V12 exam with ease.