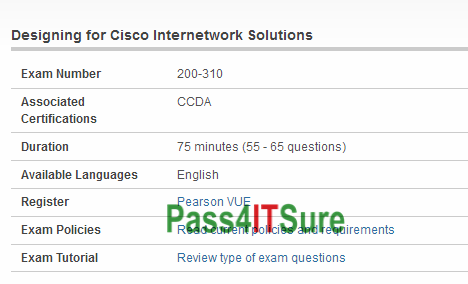
How can I study for the Cisco 200-310 dumps? The Designing for Cisco Internetwork Solutions (200-310 DESGN) exam is a 75 minutes (55 – 65 questions) assessment in pass4itsure that is associated with the CCDA certification. New real Cisco CCDA 200-310 dumps exam Designing for Cisco Internetwork Solutions practice test video is your best choice. “Designing for Cisco Internetwork Solutions” is the exam name of Pass4itsure Cisco 200-310 dumps test which designed to help candidates prepare for and pass the Cisco 200-310 exam.
With our products you can easily pass the exam. We promise that if you have used pass4itsure’s latest Cisco certification https://www.pass4itsure.com/200-310.html dumps exam questions and answers exam but fail to pass the exam, pass4itsure will give you a full refund.
[100% Pass Guarantee Cisco 200-310 Dumps From Google Drive]:https://drive.google.com/open?id=0BwxjZr-ZDwwWajNRNzNfaDllX3M
[100% Pass Guarantee Cisco 210-060 Dumps From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWNmlXYjFDT0t3UWc
★Pass4itsure Latest and Most Accurate Cisco 200-310 Dumps Exam Q&As★:
QUESTION 19
You want to gather as much detail as possible during a network audit, to include data time stamping across a large number of interfaces, customized according to interface, with a minimal impact on the network devices themselves. Which tool would you use to meet these requirements?
A. RMON
B. SNMPv3
C. NetFlow
D. Cisco Discovery Protocol
200-310 exam Correct Answer: C
QUESTION 20
Which design is the recommended geometric design for routed topologies?
A. linear
B. triangular
C. rectangular
D. circular
Correct Answer: B
QUESTION 21
Which statement is true concerning the data center access layer design?
A. The access layer in the data center is typically built at Layer 3, which allows for better sharing of services across multiple servers.
B. With Layer 2 access, the default gateway for the servers can be configured at the access or aggregation layer.
C. A dual-homing NIC requires a VLAN or trunk between the two access switches to support the dual IP addresses on the two server links to two separate switches.
D. The access layer is normally not required, as dual homing is standard from the servers to the aggregation layer.
200-310 dumps Correct Answer: B
QUESTION 22
A network engineer requires that an OSPF ASBR must only flood external LSAs only within its own area. What OSPF area type should be configured?
A. Backbone Area
B. Totally Stub Area
C. Not So Stubby Area
D. Stub Area
Correct Answer: C
QUESTION 23
Which protocol is used to reserve bandwidth for the transport of a particular application data flow across the network?
A. cRTP
B. IEEE 802.1P
C. RSVP
D. LFI
E. Auto QOS
200-310 pdf Correct Answer: C
QUESTION 24 Service Consumer A sends a request message to Service A (1) after which Service A retrieves financial data from Database
A (2). Service A then sends a request message with the retrieved data to Service
B (3). Service B exchanges messages with Service
C (4) and Service
D (5), which perform a series of calculations on the data and return the results to Service A. Service A uses these results to update Database A
(7) and finally sends a response message to Service Consumer A
(8). Component B has direct, independent access to Database A and is fully trusted by Database A. Both Component B and
Database A reside within Organization A. Service Consumer A and Services A, B, C, and D are external to the organizational boundary of Organization A. Component B is considered a mission critical program that requires guaranteed access to and fast response from Database A. Service A was recently the victim of a denial of service attack, which resulted in Database A becoming unavailable for extended periods of time (which further compromised Component B). Additionally, Services B, C, and D have repeatedly been victims of malicious intermediary attacks, which have further destabilized the performance of Service A. How can this architecture be improved to prevent these attacks?
A. A utility service is created to encapsulate Database A and to assume responsibility for authenticating all access to the database by Service A and any other service consumers. Due to the mission critical requirements of Component B, the utility service further contains logic that strictly limits the amount of concurrent requests made to Database A from outside the organizational boundary. The Data Confidentiality and Data Origin Authentication patterns are applied to all message exchanged within the external service composition in order to establish message-layer security.
B. Service Consumer A generates a private/public key pair and sends this public key and identity information to Service A. Service A generates its own private/public key pair and sends it back to Service Consumer A. Service Consumer A uses the public key of Service A to encrypt a randomly generated session key and then sign the encrypted session key with the private key. The encrypted, signed session key is sent to Service A. Now, this session key can be used for secure message-layer communication between Service Consumer A and Service A. The Service Perimeter Guard pattern is applied to establish a perimeter service that encapsulates Database A in order to authenticate all external access requests.
C. Services B, C, and D randomly generate Session Key K, and use this key to encrypt request and response messages with symmetric encryption. Session Key K is further encrypted itself asymmetrically. When each service acts as a service consumer by invoking another service, it decrypts the encrypted Session Key K and the invoked service uses the key to decrypt the encrypted response. Database A is replicated so that only the replicated version of the database can be accessed by Service A and other external service consumers.
D. The Direct Authentication pattern is applied so that when Service Consumer A submits security credentials, Service A will be able to evaluate the credentials in order to authenticate the request message. If the request message is permitted, Service A invokes the other services and accesses Database A. Database A is replicated so that only the replicated version of the database can be accessed by Service A and other external service consumers.
Answer: A
QUESTION 25 Service A exchanges messages with Service B multiple times during the same runtime service activity. Communication between Services A and B has been secured using transport-layer security. With each service request message sent to Service B (1A. IB), Service A includes an X.509 certificate, signed by an external Certificate Authority (CA). Service B validates the certificate by retrieving the public key of the CA (2A. 2B) and verifying the digital signature of the
X.509 certificate. Service B then performs a certificate revocation check against a separate external CA repository (3A, 3B). No intermediary service agents reside between Service A and Service B. To fulfill a new security requirement, Service A needs to be able to verify that the response message sent by Service B has not been modified during transit. Secondly, the runtime performance between Services A and B has been unacceptably poor and therefore must be improved without losing the ability to verify Service A’s security credentials. It has been determined that the latency is being caused by redundant security processing carried out by Service B. Which of the following statements describes a solution that fulfills these requirements?
A. Apply the Trusted Subsystem pattern to introduce a utility service that performs the security processing instead of Service B. The utility service can verify the security credentials of request messages from Service A and digitally sign messages sent to Service A to enable verification of message integrity. Furthermore, the utility service can perform the verification of security credentials submitted by Service A only once per runtime service activity. After the first messageexchange, it can issue a SAML token to Service A that gets stored within the current session. Service A can then use this session-based token with subsequent message exchange. Because SAML tokens have a very small validity period (in contrast to X.509 certificates), there is no need to perform a revocation check with every message exchange.
B. Service B needs to be redesigned so that it performs the verification of request messages from Service A only for the first message exchange during the runtime service activity. Thereafter, it can issue a SAML token to Service A that gets stored within the current session. Service A then uses this session-based token with subsequent message exchanges. Because SAML tokens have a very small validity period (in contrast to X.509 certificates), there is no need to perform a revocation check with every message exchange.
C. WS-SecurityPolicy transport binding assertions can be used to improve performance via transport-layer security The use of symmetric keys can keep the encryption and decryption overhead to a minimum, which will further reduce the latency between Service A and Service B. By encrypting the messages, attackers cannot modify message contents, so no additional actions for integrity verification are needed.
D. The Data Origin Authentication pattern can be applied together with the Service Perimeter Guard pattern to establish a perimeter service that can verify incoming request messages sent to Service B and to filter response messages sent to Service A. The repository containing the verification information about the Certificate Authorities can be replicated in the trust domain of the perimeter service. When access is requested by Service A, the perimeter service evaluates submitted security credentials by checking them against the locally replicated repository. Furthermore, it can encrypt messages sent to Service A by Service B. and attach a signed hash value.
200-310 vce Answer: A
QUESTION: 26
Cloud Service Consumer A invokes Cloud Service A from Cloud X (owned by Cloud Provider X)
(1). To fulfill the request from Cloud Service Consumer A, Cloud Service A needs to invoke Cloud Service B that resides on Cloud Y (owned by Cloud Provider Y)
(2). After completing its processing, Cloud Service B sends a response to Cloud Service A
(3). Cloud Service A verifies the response and then finally sends its response to Cloud Service Consumer A
(4). The guaranteed availability of the Cloud Service A implementation is 95% and the guaranteed availability of the Cloud Service B implementation is 95%. Which of the following statements accurately describes the actual availability that Cloud Service Consumer A can receive based on the described scenario?
A. Because Cloud Service Consumer A’s response message is processed by two separate cloud services, the combined availability increases as follows:
1 – (1 – 0.95) X (1 – 0.95) = 0.9975 or 99.75%
B. Because Cloud Service A acts as both a cloud service and cloud service consumer in order to process Cloud Service Consumer B’s request message, Cloud Service A forms a dependency on Cloud Service B. As a result, the combined availability decreases, as follows:
0.95 X 0.95 = 0.9025 or 90.25%
C. Cloud Service Consumer A benefits from redundant cloud service implementations, thereby increasing the guaranteed availability as follows: 1 – (1 – (0.95 – 0.1))X (1 – (0.95 – 0.1)) = 0.9775 or 97.75%
D. As a result of the dependency formed by Cloud Service Aon Cloud Service B,the combined availability decreases significantly as follows: (0.95 X 0.95) – 0.1 = 0.8025 or 80.25%
Answer: B
QUESTION: 27
The cloud service owner of Cloud Service A is evaluating Clouds X, Y and Z to determine which cloud environment can offer the greatest level of reliability. All three clouds are geographically dispersed across three separate time zones. As a result, each cloud experiences usage peaks at different times. Based on the metrics provided, the greater the usage of a cloud, the lower its reliability. When the cloud service owner complains to Cloud Provider A (the owner of all three clouds) that none of the clouds provide an adequate level of reliability, Cloud Provider A suggests a solution that increases resiliency. Which of the following statements accurately describes a solution that can be used to
fulfill the resiliency requirements of Cloud Service A?
A. Redundant implementations of Cloud Service A are deployed in all three clouds. The failover system mechanism and a special type of automated scaling listener mechanism are implemented to establish a system whereby one redundant Cloud Service A implementation will automatically take over from another.
B. A cloud balancing solution is established, whereby an automated scaling listener mechanism is implemented on each cloud in such a way that every cloud can automatically scale out to another cloud. As a result, if reliability problems occur on any
one cloud, the subsequent requests will be scaled out to another cloud in a manner that is transparent to cloud service consumers.
C. A failover system mechanism is implemented on Cloud X, which acts as the primary point of contact for cloud serviceconsumers. Upon failure conditions occurring, the Cloud Service A implementation on Cloud X automatically hands over control of current and future message requests from cloud service consumers to Cloud Y. Cloud Y retains control of cloud serviceconsumer communication until the next failure condition occurs, at which point it hands over control to Cloud Z. Finally, if a failure condition occurs in Cloud Z. control is handed back to Cloud X.
D. A cloud balancing solution is established, whereby a resource replication mechanism is implemented on each cloud. This allows Cloud Service A to be automatically replicated across cloud environments, thereby enabling each implementation of Cloud Service A to take the place of another, whenever failure conditions occur.
200-310 exam Answer: A

Pass4itsure has come up with the latest training material about Cisco certification 200-310 dumps exam questions. “Designing for Cisco Internetwork Solutions”, also known as 200-310 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. Pass4itsure Cisco 200-310 dumps exam questions answers are updated (515 Q&As) are verified by experts. The associated certifications of 200-310 dumps is CCDA. Pass4itsure has provided part of Cisco certification https://www.pass4itsure.com/200-310.html exam questions and answers for you on www.pass4itsure.com and you can free download as a try.